Expressway-C Initial Configuration
While Expressway-E reboots, you can start configuring Expressway-C. This component sits on the internal enterprise network. It is the traversal client, establishing a tunnel from the inside to the Expressway-E in the edge network so that signaling can traverse the corporate firewall in both directions.
For this lab, your Expressway-C should already be configured with a system name, valid NTP server, and an internal DNS server. It also has its certificates and certificate authority certificates installed. Additionally, it has the Traversal Zones for Business to Business communication via the Expressway-E set up, as well as a zone to the Unified CM. The dial plan to use these zones is not yet set up and will be covered later as a part of this lab.
What remains to be configured is the following:
- Enable MRA
- Configure Cisco Meeting Server
- UC Client Traversal Zone
- Expressway-C Certificates
Enable Mobile and Remote Access (MRA)
As you did for Expressway-E, you need to enable MRA to enable the Web Proxy functionality. Again, you may see alerts that MRA is not configured properly or that a domain is not assigned. That is normal.
- Open the browser to the Expressway-C at https://expc1a.pod8.cms.lab
- Log in with username admin and password c1sco123.
- If prompted, click Skip Service Setup Wizard
- Navigate to Configuration > Unified Communications > Configuration
- For Unified Communications mode select Mobile and remote access
- For Authorize by OAuth token with refresh select Off
- Click Save. Other options to specify the Authentication path and Single sign-on options are not needed for our lab deployment.
Configure Cisco Meeting Server
Now that MRA is enabled, you can also configure the Cisco Meeting Server on Expressway-C.
- Navigate to Configuration > Unified Communications > Cisco Meeting Server
- Change Meeting Server Web Proxy to Enable
-
For Guest account client URI, enter the URI that users use to access the CMS Web Bridge,
join.pod8.cms.lab.
Note: If your deployment was using a non-standard port for Web Bridge (i.e. not 443), this interface does not allow you to specify a port. The only way to use a non-standard port is to use DNS SRV records. Expressway will query for an SRV record for the domain,_cms-web._tls.domain , which will return a hostname and a port. Because you are using a the standard port number, this is not necessary. - Click Save
After saving the configuration, you should see that Expressway performed a DNS query and determined what servers this URI maps to. You should see the list of all of your CMS servers on the Expressway UI.
UC Traversal Client
The Expressway-C, as mentioned earlier, is the traversal client. This means that the initial traversal link setup always occurs from the C to the E. You configured the Expressway-E with a credential (the uctraversal user you created). Now you just need to create a traversal zone to tell the Expressway-C to connect to the Expressway-E. Follow these instructions to create the traversal zone:
- Navigate to Configuration > Zones > Zones.
- Click New
- Enter in the Name field
- For the Type, select Unified Communications traversal
- In the Username field enter the user you created earlier on the Expressway-E.
- In the Password field enter If pasting this value, use Control-V
- For the SIP Port, enter
- In the Location section, for Peer 1 address enter the FQDN of the Expressway-E, . If the Expressway-E were a cluster, all other members would be explicitly listed on separate peer addresses.
- Click Create Zone
You can refresh this information a few times, and eventually the zone should go Active.
Expressway-C Certificates
The reason the UC Traversal Zone went to a Active state is because the Expressway-E trusted the Expressway-C's certificate. Remember that the Expressway-E has the Certificate Authority that signed the Expressway-C's certificate in its Trusted Certificate Authority list. Secondly, the Expressway-C trusted the certificate that the Expressway-E presented.
Trusted Certificate Authority Certificates
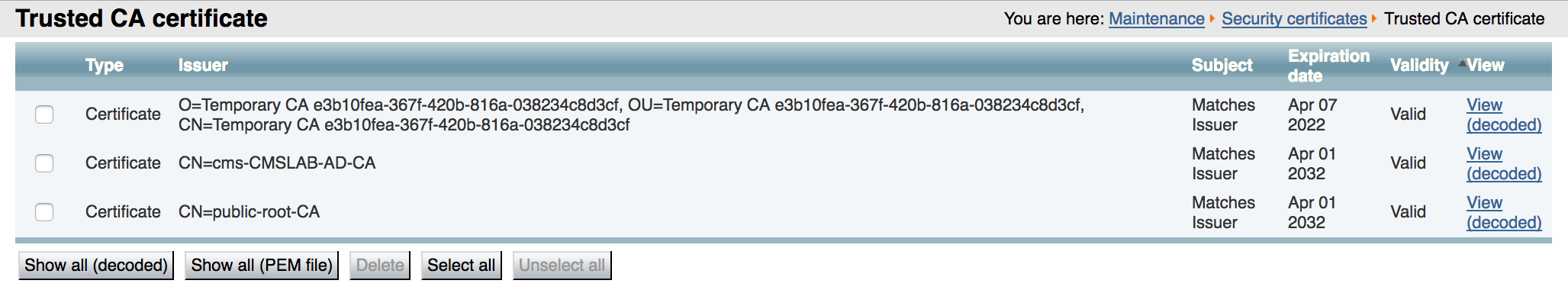
Open the browser to the Expressway-C and navigate to Maintenance > Security > Trusted CA certificate. You should see the self-signed CA certificate ("Temporary CA"), the cms-CMSLAB-AD-CA, which signs the internal server certificates, such as the CMS servers and Unified CM, as well as the public-root-CA certificate which will allow us to trust the certificate that the Expressway-E presented to us.
Expressway-C Server Certificate
The Expressway-E server certificate has already been installed. For the Web Proxy feature there are no special requirements for it. In this lab, it is signed by the internal, private Certificate Authority (cms-CMSLAB-AD-CA). This is important since you will have encrypted communication and calls everywhere.